Shared folders, network computers, flash drives, discs on the "Network" tab of Windows Explorer are not displayed. Disable SMB1 for Windows Protects with Windows from Attack Switching on SMB 2 Windows 10 Protocol
If you are from Windows 10, you cannot open network folders on other network devices (NAS, SAMBA Linux Server) or on computers with old Windows versions (Windows 7 / XP / 2003), most likely the problem is due to the fact that in your new version of Windows 10 Disabled support for outdated and unsafe versions of the SMB protocol (used in Windows to access common network folders and files). So, starting with Windows 10 1709, the SMBV1 protocol and anonymous (guest) access to network folders via SMBV2 was disabled.
Microsoft systematically disables old and unsafe versions of the SMB protocol in all the latest versions of Windows. Starting with Windows 10 1709 and Windows Server 2019 (both in Datacenter and in Standard) in operating system By default (remember the attack, which was just implemented through the hole in SMBV1).
Specific steps that need to be taken depend on the error that appears in Windows 10 when accessing a shared folder and from the remote SMB settings of the server on which is stored common folders.
You can not get a guest access to the shared folder without authentication
Starting with the version of Windows 10 1709 (Fall Creators Update.) Enterprise and Education Users began to complain that when trying to open a network folder on a nearby computer, an error began to appear:
You cannot access this shared folder, as your organization security policies block guest access without authentication. These politicians help protect your computer from unsafe or malicious devices on the network. AN. error Occurred. While ReconNecting Y: To \\\\ NAS1 \\ Share Microsoft Windows. Network: You Can't Access This Shared Folder Because Your Organization's Security Policies Block Unauthenticated Guest Access. These Policies Help Protect Your PC from Unsafe or Malicious Devices on The Network.

With it on other computers with old versions of Windows 8.1 / 7 or on Windows 10 with builds to 1709, the same network directories open normally. This problems are related to the fact that modern versions Windows 10 (starting from 1709) by default is prohibited network access Network folders under the guest account on the SMBV2 protocol (and below). Guest (anonymous) access implies access to a network folder without authentication. When accessing the SMBV1 / V2, the SMBV1 / V2 protocol does not apply such traffic protection methods as SMB signing and, making your session vulnerable vs. MITM (man-in-the-middle) attacks.
When you try to open a network folder under a guest by SMB2, an error is recorded in the SMB client log (Microsoft-Windows-SMBClient):
SOURCE: Microsoft-Windows-Smbclient Event ID: 31017 Rejected An Insecure Guest Logon.
In most cases, this problem can be encountered when using old versions of NAS (usually for ease of configuration, guests include guest access) or when accessing network folders on old versions of Windows 7/2008 R2 or Windows XP / 2003 with configured (guest) access ( See different versions of Windows).
In this case, Microsoft recommends changing the settings on remote computer or NAS device that distributes network folders. It is advisable to switch the network resource into SMBV3 mode. And if only the SMBV2 protocol is supported, configure access with authentication. It is the most correct and safe method Fix the problem.
Depending on the device on which network folders are stored, you must disable guest access to them.

There is another way - change the settings of your SMB client and allow access to network folders under the guest account.
To allow guest access to your computer, open the group policy editor (gpedit.msc) and go to: Computer Configuration -\u003e Administrative Templates -\u003e Network -\u003e LANMAN Workstation ( Computer Configuration -\u003e Administrative Templates -\u003e Network -\u003e Lanman Workstation). Enable policies Enable Insecure Guest Logons (Include Insecure Guest Inputs).

Those. From the error message, it is clearly seen that the network folder only supports the SMBV1 access protocol. In this case, you need to try to reconfigure the remote SMB device to support at least SMBV2 (correct and safe way).
If the network folders distribute Samba to Linux, you can specify the minimum supported SMB version in the SMB.conf file as follows:
Server Min Protocol \u003d SMB2_10 Client Max Protocol \u003d SMB3 Client Min Protocol \u003d SMB2_10 Encrypt Passwords \u003d True Restrict Anonymous \u003d 2
In Windows 7 / Windows Server 2008 R2, you can disable SMBV1 and resolve SMBV2 as follows:
Set-ItemProperty -path "HKLM: \\ System \\ CurrentControlSet \\ Services \\ Lanmanserver \\ Parameters" SMB1 -Type DWORD -Value 0 -Force
Disable-WindowsOptionalFeature -Online -FeatureName "SMB1PROTOCOL"
SET-SMBServerConfiguration -Enablesmb2Protocol $ True
If your network device (NAS, Windows XP, Windows Server 2003) supports SMB1 protocol, in Windows 10, you can enable a separate SMB1Protocol-Client component. But it is not recommended !!!
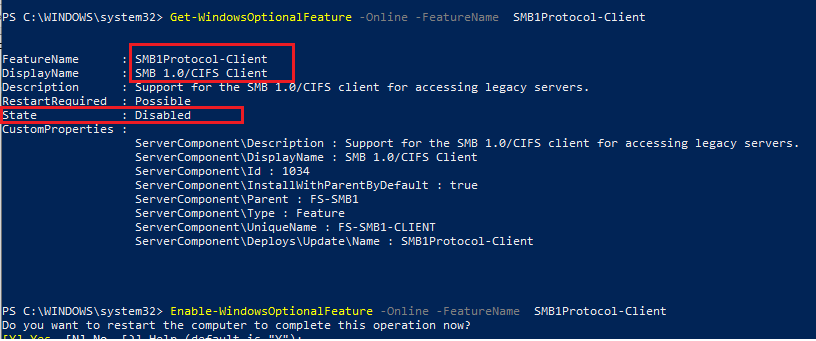
Run the PowerShell Console and check that SMB1Protocol-Client is disabled (State: Disabled):
Get-WindowsOptionalFeature -Online -FeatureName Smb1Protocol-Client
Enable SMBV1 Support (Restart):
Enable-WindowsOptionalFeature -Online -FeatureName Smb1Protocol-Client
You can also enable / disable additional windows components 10 (including SMBV1) from the OptionalFeatures.exe menu -\u003e SMB 1.0 / CIFS File Sharing Support

In Windows 10 1709 and above, the SMBV1 client is automatically deleted if it has not been used for more than 15 days (the SMB 1.0 / CIFS Automatic Removal component is responsible for it.
In this example, I turned on only the SMBV1 client. Do not turn on the SMB1PROTOCOL-Server component if your computer is not used outdated customers as a server for storing public folders.
After installing the SMBV1 client, you must easily connect to a network folder or printer. However, it is necessary to understand that the use of this workaround is not recommended, because exposes your system of danger.
In connection with the recent epidemic encipher Wannacry.operating the SMB V1 vulnerability, the network again appeared tips on the disconnection of this protocol. Moreover, Microsoft strongly recommended Disable the first SMB version back in September 2016. But such a shutdown can lead to unexpected consequences, up to curiosity: personally came across the company, where after the fight against SMB stopped playing wireless columns Sonos.
Especially to minimize the likelihood of "foot-in-foot", I want to remind the features of the SMB and consider in detail how the ill-conceived shutdown of its old versions is.
SMB. (Server Message Block) - Network Protocol for remote access to files and printers. It is it used when connecting resources through \\ ServerName \\ ShareName. The protocol initially worked on top of NetBIOS using the UDP ports 137, 138 and TCP 137, 139. The Windows 2000 output began to work directly using the TCP 445 port. SMB is also used to enter the Active Directory domain and work in it.
In addition to remote access to resources, the protocol is also used for interprocessor interaction through "named streams" - Named Pipes. Process appeal is made along the path \\. \\ Pipe \\ Name.
The first version of the protocol, also known as CIFS (Common Internet File System), was created back in the 1980s, and here the second version appeared only with Windows Vista.In 2006. The third version of the protocol came out with Windows 8. In parallel with Microsoft, the protocol was created and updated in its open Implementation of Samba.
Each new version of the protocol was added different kinds of improvements aimed at increasing speed, security and support for new features. But the support of old protocols for compatibility remained support. Of course, there were enough vulnerabilities in old versions, one of which uses Wannacry.
Under the spoiler, you will find a summary table of changes in SMB versions.
| Version | Operating system | Added, compared with the previous version |
| SMB 2.0 | Windows Vista / 2008 | Changed the number of protocol commands from 100+ to 19 |
| The ability to "conveyor" work - sending additional queries before receiving an answer to the previous | ||
| Support symbolic links | ||
| Signature of HMAC SHA256 messages instead of MD5 | ||
| Increase cache and records / reading blocks | ||
| SMB 2.1. | Windows 7 / 2008R2 | Performance improvement |
| Support more MTU | ||
| BranchCache Support - Mechanism, Casual Requests in the Global Network On Local Network | ||
| SMB 3.0 | Windows 8/2012 | The possibility of constructing a transparent fault tolerant cluster with load distribution |
| Memory Direct Access Support (RDMA) | ||
| Management through PowerShell cmdlets | ||
| Support VSS. | ||
| Signature AES-CMAC | ||
| AES-CCM Encryption | ||
| Ability to use network storage folders virtual machines Hyperv. | ||
| Ability to use network folders for storing Microsoft SQL databases | ||
| SMB 3.02 | Windows 8.1 / 2012R2 | Improving safety and speed |
| Automatic balancing in the cluster | ||
| SMB 3.1.1 | Windows 10/2016 | AES-GCM Encryption Support |
| Checking integrity to authentication using hash SHA512 | ||
| Mandatory safe "negotiations" when working with SMB 2.x clients and above |
We consider conditionally affected
View currently used version of the protocol is quite simple, we use the cmdlet for this Get-Smbconnection.:

Output of cmdlet when open network resources on servers with visible version Windows.
From the output it is clear that the client supporting all versions of the protocol uses to connect the highest possible version from the server supported. Of course, if the client supports only old version Protocol, and on the server it will be disabled - the connection will not be installed. Enable or disable the support of old versions in modern systems Windows can be using a cmdlet Set-SMBServerConfiguration., And see the Condition like this:
Get-SMBServerConfiguration | SELECT ENABLESMB1PROTOCOL, ENABLESMB2PROTOCOL

Turn off the SMBV1 on the server with Windows 2012 R2.

Result when connected with Windows 2003.
Thus, when the old, vulnerable protocol is disconnected, the network operability with old customers can be lost. At the same time, in addition to Windows XP and 2003 SMB V1, both in a number of software and hardware solutions (for example, NAS on GNU \\ Linux, using the old Samba version).
Under the spoiler, I will give a list of manufacturers and products that are fully or partially stopped working when SMB V1 is disconnected.
| Manufacturer | Product | Comment |
| Barracuda. | SSL VPN. | |
| Web Security Gateway Backups | ||
| Canon | Scanning on a network resource | |
| Cisco. | WSA / WSAV | |
| Waas. | Version 5.0 and older | |
| F5. | RDP Client Gateway. | |
| Microsoft Exchange Proxy. | ||
| Forcepoint (Raytheon) | "Some products" | |
| HPE | ARCSIGHT LEGACY UNIFIED CONNECTOR | Old version |
| IBM. | NetServer | Version V7R2 and older |
| QRADAR VULNERABILITY MANAGER. | Version 7.2.x and older | |
| Lexmark. | Firmware Firmware ESF 2.x and ESF 3.x | |
| Linux Kernel. | CIFS client | From 2.5.42 to 3.5.x |
| McAfee | Web Gateway. | |
| Microsoft. | Windows | XP / 2003 and older |
| Myob | Accountants. | |
| Netapp | ONTAP | Version up to 9.1. |
| NetGear. | READYNAS. | |
| Oracle | Solaris. | 11.3 and older |
| Pulse Secure | PCS. | 8.1R9 / 8.2R4 and older |
| PPS | 5.1R9 / 5.3R4 and older | |
| QnaP. | All storage devices | Firmware older 4.1. |
| Redhat. | Rhel. | Versions up to 7.2. |
| Ricoh. | MFP, scanning on a network resource | In addition to a number of models |
| RSA. | Authentication Manager Server | |
| Samba. | Samba. | Over 3.5. |
| Sonos. | Wireless columns | |
| Sophos. | Sophos UTM. | |
| Sophos XG Firewall | ||
| Sophos Web Appliance | ||
| SUSE. | Sles. | 11 and older |
| Synology. | DiskStation Manager. | Only management |
| Thomson Reuters. | CS Professional Suite. | |
| Tintri. | TINTRI OS, TINTRI GLOBAL CENTER | |
| Vmware. | Vcenter. | |
| ESXI. | Older 6.0 | |
| Worldox. | GX3 DMS. | |
| Xerox. | MFP, scanning on a network resource | Firmware without ConnectKey Firmware |
The list is taken from the Microsoft website, where it is regularly replenished.
The list of products using the old version of the protocol is quite large - before disabling SMB V1, you must think about the consequences.
Still turn off
If programs and devices using SMB V1 are not in the network, then, of course, the old protocol is better disconnected. In this case, if you turn off on SMB windows server 8/2012 is performed using the PowerShell cmdlet, then the registry edit will be needed for Windows 7/2008. This can also be done with PowerShell:
Set-ItemProperty -path "HKLM: \\ System \\ CurrentControlSet \\ Services \\ Lanmanserver \\ Parameters" SMB1 -Type DWORD -Value 0 -Force
Or any other in a convenient way. At the same time, it will take a reboot to apply changes.
To disable SMB V1 support on the client, it suffices to stop the service responsible for its operation and correct the dependence of the LanManWorkStation service. This can be done by the following commands:
SC.exe Config LanmanworkStation Depend \u003d Bowser / MrxSMB20 / NSI SC.exe Config MRXSMB10 Start \u003d Disabled
For the convenience of disconnecting the protocol throughout the network, it is convenient to use group policies, in particular Group Policy Preferences. With the help of them you can conveniently work with the registry.

Creating a registry element through group policies.
To disable the protocol on the server, it is enough to create the following parameter:
- meaning: 0.
path: HKLM: \\ System \\ CurrentControlset \\ Services \\ LanmanServer \\ Parameters;
new parameter: REG_DWORD C name SMB1;

Creating a registry parameter to disable SMB V1 on a server through group policies.
To disable SMB V1 support, you need to change the value of two parameters.
First, disable the SMB V1 Protocol service:
- meaning: 4.
path: HKLM: \\ System \\ CurrentControlSet \\ Services \\ MRXSMB10;
parameter: REG_DWORD C name Start;

We update one of the parameters.
Then we will correct the dependence of the LanManWorkStation service, so that it does not depend on SMB V1:
- value: Three lines - Bowserve, MRXSMB20 and NSI.
path: HKLM: \\ System \\ CurrentControlSet \\ Services \\ LanManWorkStation;
parameter: REG_MULTI_SZ named DependonService;

And replace the other.
After use group Policy It is necessary to restart the computers of the organization. After rebooting SMB V1 will stop being used.
Works - do not touch
Oddly enough, this old commandment is not always useful - in rarely updated infrastructure, encrypters and trojans can start. Nevertheless, the inaccurate shutdown and service updates can paralyze the organization of the organization is not worse than viruses.
Tell us, have you already disabled SMB first version? Have a lot of victims?
This article describes how to set up sharing, files and folders, without a password on Windows 10.
This instruction will consider the simplest case of setting up shared access to Windows 10 folders. When you need to provide access to the shared Windows 10 resources without a password. This is the most common situation in home networks and a small office network. This setting assumes that access over the network will be without a password, without restrictions.
Note. If you have Windows 10 2017 or 2018 and you encountered a problem " Windows 10 does not see other computers on the local network", then, read another article - it describes how to solve the problem with connecting Windows 10 to the old versions of Windows. This article may be relevant for windows connections 10 to the old versions of Linux.
But at the beginning of a silent theory.
Local and global networks
Global computer network, today, there is only one, it is the Internet. Local computer networks differ from the global investigators:
- Quantities of computers united in this network.
- The quantity and quality of shared (available) in this network of resources.
IN global Network The Internet combined hundreds of millions (possibly more than a billion) computers. These computers provide a large number of resources in different ways. The most common of which is text and graphic information. In addition to the Internet itself, this information is also possible - there are services to work with images and documents. Also on the Internet services are available not related to computer subjects, such as selling goods and services (for example, the sale of tickets for various transports).
In local computer network Most often combines from two to several computers. Much less often the number of computers in the local network can be several dozen or hundreds (in large commercial or state organizations). As a rule, only a few resources are distributed in local networks - files, printers, scanners and Internet access.
Physically computers are combined into a network or using a cable or through a radio signal (WiFi). But in any case, the local network configuration is performed equally.
So, what, and in what sequence, you need to do in order to configure the Windows 10 network?
Sharing Windows 10 without password
In this manual, it will be described how to configure the Windows 10 network so that the shared access to folders (files) and printers is provided without a password request. This is a version of the trusted network. This organization of the local computer network is most convenient to use (no need to memorize passwords for each computer). And besides, such a network is easier to create and maintain.
Start setting up the local network is best with the verification of the necessary conditions.
Verify connection on the local network
First you need to check the availability of connection on a local network. To do this, open the applet of available network adapters and network connections. The easiest way to open this applet through the dialog box " Perform Windows + R. nCPA.cpl and click " OK":
Note: There is a longer way - to open "" and shout there on the link " Change adapter settings".
This is how the network connections applet looks like:

This example shows that the physical network adapter on the computer has and the network connection to the local network is also there. This example uses a cable connection to the LAN (Ethernet). In case of connection through WiFi adapter will be called " Wireless connection 802-11".
Possible errors that can be detected in the "Network Connections" apple:
- In this applet, it may not be adapters at all - in this case, you need to check the list of equipment (Device Manager). It is possible a network adapter is disabled or drivers are not installed.
- Adapter can be crossed out with a red cross. This means that there is no physical connection to the local network. You need to check the cables. In the case of WiFi, this means that the computer is not connected to the access point (router) WiFi.
- The adapter may have an inscription " Unidentified Network". This means that there is a physical connection to the local network, but the computer could not get the settings of this network. Most often it happens if there is no router on the local network and manually specify the parameters of the local network.
By the default of Windows Configured to automatically receive network settings from a network router. If there is a router on the local network, then it's enough for you network cable Or connect to WiFi access point. If there is no router on the local network, and it sometimes happens when using small cable networks, then you need to manually specify network settings in properties network adapter. More details on manual setting of the parameters of the local network written in the article "Setting the network between Linux and Windows". There is a configuration for Windows XP, but for Windows 10 will be the same.
The next step is to check the computer name and working Group. To do this, you need to open the applet " Properties of the system". The easiest way to open this applet through the dialog box" Perform". It is available through the Start menu or when you press keys Windows + R. on keyboard. Write in this window sysdm.cpl and click " OK":

This is what the applet looks like " Properties of the system"(You need to open the tab" Computer name"):

Here you need to check:
- Full name - It should not be written by Cyrillic and should not have gaps.
- Working group - It should not be written by Cyrillic and should not have gaps. In addition, the name of the Working Group should coincide with the same name on other LAN computers. That is, the name of the working group should be equally on all computers of the local network.
If you need to change the computer name or working group, click the Edit button. After such a change, you will need to reboot Windows.
Now you can go to the setup windows networks 10.
Setting up Windows 10 network
Open "Windows Explorer" And find and open it in it. " Net". By default, Windows 10 is disabled on Windows 10 and when you open the" Network ", at the top there will be a warning inscription:

You need to click on this inscription and then choose the item " Enable network detection and sharing files":

Note: Another way to enable network detection and sharing files through " Network and Shared Access Control Center"And there shout on the link" Advanced shared access parameters"And then open the desired profile.
Thereafter "Windows Explorer" I will give a request to choose a network type, there you need to select the first option:

Note: If you later need to change the type of network - the instruction in the article "Change Windows 10 Type".
Thereafter "Windows Explorer."Shows a list of computers on the local network:

Now you can enter those folders on these computers for which you have a common access.
Entry through local network On the computer named "Home":

Next step - you need to configure sharing to Windows 10 folders.
How to configure sharing Windows 10 folder
IN "Windows Explorer."Find the folder for which you want to provide sharing. Click on this folder right mouse button and select the item menu. Properties"(In this illustration, the folder is called LAN):

Note: The name of the folder must be a latin and without spaces.
In the folder properties window, you need to open the tab " Access"And there click the button" General access":

In the next window, you need to open a list of local users (accounts on this computer) and select "All" in this list:

After that click the "Add" button:

After that, it is necessary for the "All" group, specify read and write access rights:


After that, click the "Done" button:

After that, the window will be open again. " Folder properties". In it you can check the tab" Safety", there must be full access for the group" Everything"(Windows automatically changes the rights of the file nTFS systems):

All, on this setting access to specific folder Finished. If you want to solve some other folder, these actions need to be repeated for each.
Note: Shake separate files not necessary. All files that are in a shared folder will be available over the network. Will also be available over the network and all nested Folders.
Last action remains ..
Need to open " Network and Shared Access Control Center"And on the left side to click on" Change extra options General access":

In the next window you need to open profile " All networks":

And there turn off the parameter " common Access with Password Protection"And of course click the" Save Changes "button:

This is configured to access the network without a password for Windows 10 completed. Now you can go through the local network to this computer and Windows will not require the password input.
To check, go to the Windows 10 computer from the Windows XP computer:

The shared folder "LAN" opens and can be in it, via the local network, edit and create files.
But if, however, Windows requires a network password
Despite the fact that the settings that are described above are made when entering this computer, another computer can request network password. This is possible in two cases.
Local users with the same name (login)
Both computers have local users with the same name, but with different passwords.
Example. There are COMP1 and COMP2. Each of them has a user named User. But on COMP1 from the user Password 123, and on comp2 it has a password of 456. When attempting a network login, the system will request a password.
Decision. Or remove matching user logins. Or for users with the same login, specify the same password. An empty password is also considered the same.
On Windows 10 there is no local user
On Windows 10, you can log in and working with Microsoft account, if there is an Internet. This situation is possible when you install the local user at all when Windows 10 is installed (input was through account microsoft recording). In this case, Windows will also require a password when entering the local network.
Decision. Create a local user on Windows 10.
If your local network has old computers
If your local network has computers running old versions of Windows or Linux, then you may encounter a problem when Windows 10 does not see such computers.
The reason may be that recent versions Windows 10 disconnected support for SMB version 1. How to enable support for SMB version 1, written in the Local Network Between Windows 10 and Windows XP.
Cancel Sharing Windows 10 folder
On Windows 10, the cancellation of the total access is made at all obvious (unlike Windows XP). On the tab " Access"(Folder Properties) No option, as it was in Windows XP. The" Sharing "button is useless, it is not possible to cancel sharing.
Now, to cancel a shared access, you need to tab Access"Press the button" Extended setting":

And there disable access (remove the bird on the "Open access to this folder" options):

As they say, "Guess three times."
Share access to the Windows 10 folder via the command line
Everything can be done much faster if used command line (console, cmd.exe). Total two teams:
nET Share Lan \u003d C: \\ LAN
nET SHARE LAN / DELETE
The first command opens sharing folder C: \\ LAN and asks for her network name LAN.
The second command deletes the network (public) folder LAN. Real folder c: \\ LAN Of course it remains in place.
Share Windows 10 files through the "Shared Folders" snap
Included tools windows management 10 is special program (Snap) to manage common resources on the computer. It is called "Shared Folders" and can be launched by a team fsmgmt.msc. (in the console or through Win + R):

On another, this snap can be opened through the Start menu: "Control Panel - Administration - Computer Management - Shared Folders."
Share access to Windows 10 printers
Sharing printers is configured in the same way as for the folder. You need to open the applet "Devices and Printers", find the desired printer there, open its properties and on the "Access" tab to determine network access settings.
Setting up a local network for other OS
If you live in Krasnodar and you need to configure the local network in Windows
Ivan Sukhov, 2017, 2019 .
If you were useful or just liked this article, then do not hesitate to support the author's material. It's easy to do throwing money on Yandex wallet number 410011416229354. Or on the phone +7 918-16-26-331 .
Even a small amount can help writing new articles :)
The default in Windows 10 and in Windows Server 2016 is still enabled support for SMB 1.0. In most cases, it is required only to ensure the work of outdated systems:, Windows Server 2003 and older. In the event that there are no such customers on your network, it is desirable to disable the SMB 1.x protocol in new versions of Windows, or completely delete the driver. Thus, you will protect against a large number of vulnerabilities that are peculiar to this outdated protocol (as once again testifies), and all customers when accessing SMB balls will use new more productive, secure and version of the SMB protocol.
In one of the previous articles, we led to the client and server side. According to the table, old versions of customers (XP, Server 2003 and some obsolete * NIX clients) can only use SMB 1.0 protocol to access file resources. If there are no such clients on the network, you can completely disable SMB 1.0 on the file server side (including the AD domain controllers) and client stations.
Audit access to the file server for SMB V1.0
Before turning off I. full removal SMB 1.0 driver. On the file SMB file SMB, it is advisable to make sure that there are no obsolete clients that are connected to it by SMB V1.0. To do this, we will turn on the audit of access to the file server for this protocol using the PowerShell command:
Set-SMBServerConfiguration -AuditSMB1ACCESS $ True
After some time, learn the events in applications and Services magazine -\u003e Microsoft -\u003e Windows -\u003e SMBServer -\u003e Audit For client access using the SMB1 protocol.
Council. The list of events from this journal can be displayed as a command:
Get-WinEvent -Logname Microsoft-Windows-SMBServer / Audit
In our example, the magazine recorded access from the client 192.168.1.10 by the SMB1 protocol. This is evidenced by events with EventID 3000 from the SMBServer source and description:
SMB1 Access.
Client Address: 192.168.1.10
Guidance:
This Event Indicates That A Client Attempted to Access The Server using SMB1. To Stop Auditing SMB1 Access, Use the Windows PowerShell Cmdlet Set-SMBServerConfiguration.
In this case, we ignore this information, but you need to consider the fact that in the future this client It will not be able to connect to this SMB server.
Disable SMB 1.0 on the server side
The SMB 1.0 protocol can be disconnected both on the client side and on the server side. On the server side, the SMB 1.0 protocol provides access to SMB network folders (file balls) over the network, and the client side is needed to connect to such resources.
Using the following PowerShell command, check if the SMB1 protocol on the server side is enabled:
 As you can see, the value of the variable is EnableSmb1Protocol \u003d True.
As you can see, the value of the variable is EnableSmb1Protocol \u003d True.
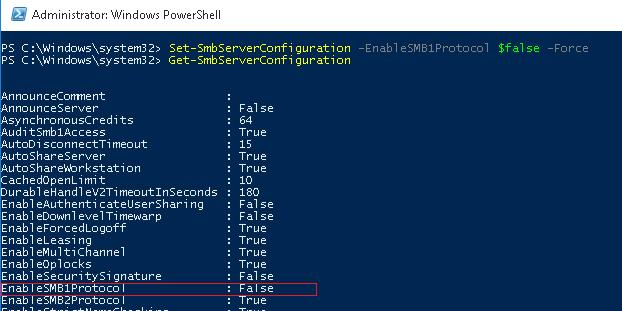
So, we will disable support for this Protocol:
SET-SMBSERVERCONFIGURATION -ENABLESMB1PROTOCOL $ FALSE -FORCE
And using the Get-SMBServerConfiguration cmdlet, make sure that the SMB1 protocol is now turned off.
To completely remove the driver processing client access via SMB V1, run the following command:
Disable-WindowsOptionalFeature -Online -FeatureName SMB1PROTOCOL -REMOVE
It remains to restart the system and make sure that support for the SMB1 protocol is completely disabled.
Get-WindowsOptionalFeature -Online -FeatureName SMB1PROTOCOL

Disable SMB 1.0 on the client side
Disabled SMB 1.0 on the server side, we achieved the fact that customers will not be able to connect to it on this protocol. However, they can use an outdated protocol to access third-party (including external) resources. To disable SMB V1 support on the client side, run:
sC.exe Config LanmanworkStation Depend \u003d BowSer / MRXSMB20 / NSI
sC.exe Config MrxSMB10 Start \u003d Disabled
So, disabling the support of the outdated SMB 1.0 on the customer and servers side, you cavity protect your network from all known and not yet found vulnerabilities in it. And Vulnerabilities B. Microsoft Server Message Block 1.0 find quite regularly. The last substantial vulnerability in SMBV1, allowing an attacker to remotely perform arbitrary code, was fixed in March 2017.
This fall Microsoft plans to completely disable the SMBV1 protocol in Windows 10.
Network Protocol The SMB of the first version was designed by Microsoft for a couple of dozen years ago. The company clearly realizes that the days of this technology have long been discussed.
However, this change will only affect new windows installations 10. If you simply update to Windows 10 Fall Creators Update, the protocol will still remain in the system.
In the Windows 10 test assembly, the Insider Preview Build 16226 SMBV1 is already completely disconnected. In versions of home and Pro, the server component is deleted by default, but the SMB1 client is still in the system. This means that you can connect to devices via SMB1, but no one can connect to your machine on it. In the versions of Enterprise and Education SMB1 completely disabled.
Ned Pyle from Microsoft explained that the main reason for this decision was to increase the level of safety:
"This is the main, but not the only reason. The old protocol was replaced by a more functional SMB2, which provides more opportunities. Version 2.02 comes with Windows Server 2008 and is the minimum recommended SMB version. To get maximum security and functionality, it is worth using the SMB version 3.1.1. SMB 1 has long been morally outdated. "
Although SMBV1 still remains on devices updated to Windows 10 Fall Creators Update, it can be disabled manually.
How to disable SMB1 in Windows 10
- Type in search Many Start Control Panel And go to "Programs and Components".
- In the left menu, select the "Enable and Disable Windows Components" option.
- Remove the checkbox near the object " Sharing SMB 1.0 / CIFS File Support”.

or using PowerShell:
- Right-click on the Start menu, select the option. Windows PowerShell (Administrator)
- Run the DISABLE-WindowsOptionalFeature -Online -FeatureName SMB1PROTOCOL command

 entrance
entrance